Greetings investigators! You’ve no doubt come across a variety of tools and services that search social media sites, from Facebook to Github, to find registered users and/or emails.
In this blog post, we will go over how such tools and services work, and show you how you can easily fit SOCMINT (SOCial Media Intelligence) checks in your investigative workflow.
There are lots of such tools: Holehe, Sherlock, Maigret, Social Analyzer etc, and most of them function in a similar way. In this blog post we will look at a tool called ‘WhatsMyName’ by WebBreacher, as its simple and straightforward structure makes it easy to explain. The tool itself is available here: Link.
The Github repository of the tool has a lot of files, but we only really need to look at one: ‘web_accounts_list.json’. The file looks a little bit like this:
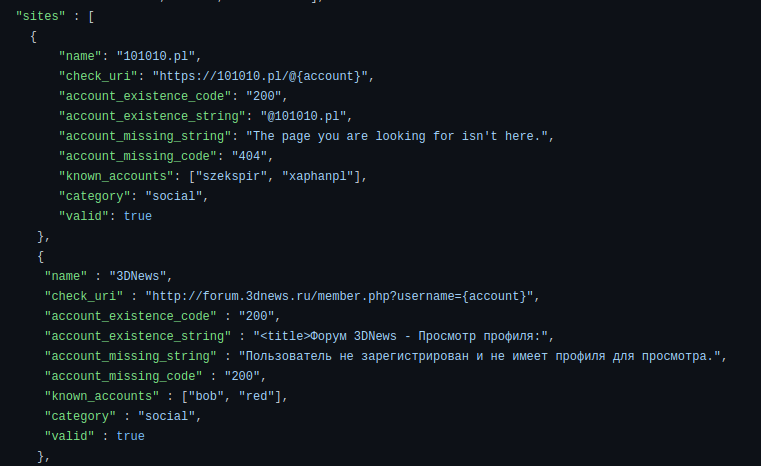
The main part of the file is a list of sites to check for account names. For example, if you’re looking for someone with the username ‘Test123’ on the website ‘101010.pl’, you would visit the URL ‘https://101010.pl/@Test123’.
Sites often behave differently when you enter valid information versus when you enter invalid information. In this case, if the username you are checking exists on the website, you will get a response with the user’s profile, which would contain the string ‘@101010.pl’. If the username does not exist, you will instead get a response with the string: ‘The page you are looking for isn’t here.’:
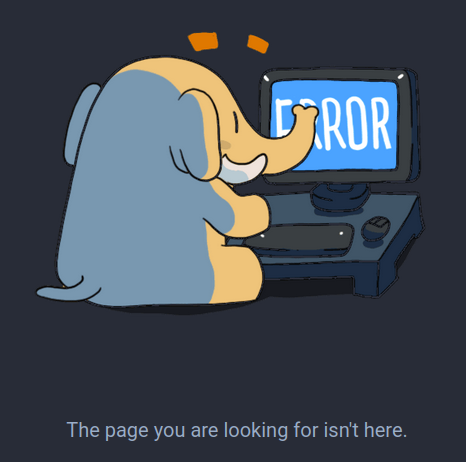
By checking what response you get from the website, you can validate whether a username exists or not. HTTP Status Codes (i.e. 200 OK, 404 Not Found) can often tell you if a page exists or not just by themselves, though that is not always reliable.
Of course, there can be false positives in the case that the test is not strict enough. Furthermore, some sites, especially ones belonging to prominent companies, are very diligent when it comes to security. If a site returns the same response for both registered and non-registered users, we cannot determine if an account on that site exists.
Not all sites can be enumerated by simply visiting a link to a profile. Some sites don’t even function without Javascript, so sending a request to a URL through the commandline is not always going to give good results, if it gives any at all. A lot of tools omit sites that require user interaction, as interacting with a website often requires emulating a browser. So, how would one go about checking for accounts on these types of sites?
Fortunately for us, social media sites frequently sacrifice some security for usability, and give us information to help us deduce whether someone signed up for the site or not.
If you ever forgot your login details for a site, you’ve probably been told by the website that your username or password was incorrect. This is proper behavior, since it obfuscates whether a user actually exists or not.
But what happens if you try to log in, and the site instead tells you this:
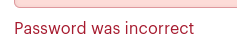
You now know that the user you’ve been trying to log in as exists! Knowing what sites your target uses could be invaluable for an investigator, as criminals often are not diligent enough when it comes to scrubbing their social media presence.
Of course, checking each site individually is a lot of work; which is where tools come in. There is a large variety of social media querying tools, but some of the open source ones that are frequently mentioned are Holehe, WhatsMyName, MailCat, Social Analyzer and Snscrape. These tools will query a large number of sites and give you results that you can follow up on.
As mentioned before however, the tools mentioned do not work with sites that require Javascript-based interaction. There are very few tools available that emulate browsers for the purposes of account enumeration. Such tools typically use libraries like Playwright, Puppeteer and Selenium in order to appear as a genuine browser user to websites.
Even fewer tools take the necessary precautions to evade bot detection and avoid triggering CAPTCHA prompts. A lot of the anti-bot measures are kept secret by the companies implementing them, but some researchers have made test websites that let you see how ‘human’ your bot is. These can serve as a good starting point for anti-bot evasion. One of them is available here: Link.
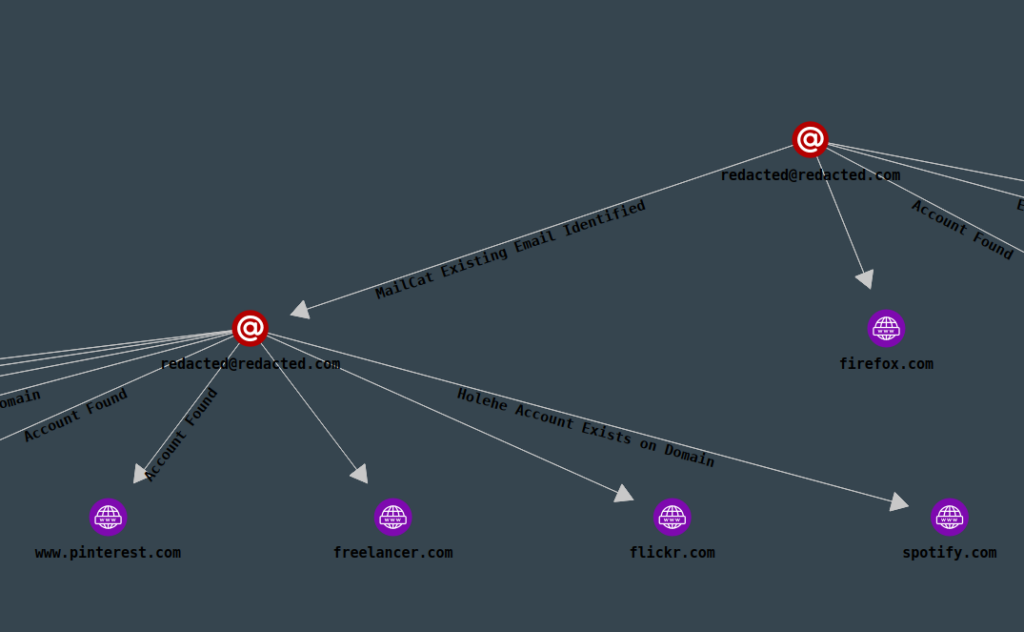
Even after using tools to find accounts, you will have a dozen reports, all in different formats, that you now have to link together, deduplicate, check for correctness, and follow up on. This is busywork that we believe investigators should not have to do. For that reason, we have integrated all the SOCMINT tools we mentioned (and more!) into LinkScope, including a Javascript (JS) based account check:
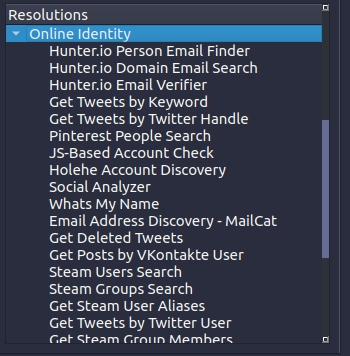
Everything found by each of the tools will be presented in a nice graph, showing you how your findings are connected, and help you pivot from your information in just a few seconds:
We also have an introductory blog post if you’re new to using LinkScope, available here: Link.
As a last piece of advice, note that no matter what tools you choose to use, it is important that you run checks like these from a clean workstation. A Virtual Machine with a fresh Operating System installation (that is, you have not done anything with the Virtual Machine yet) is the best working environment for investigations. If your working environment is not clean, the tools you run that try to detect the existence of accounts might run into issues.
An example of an issue you might run into, is that if you’ve previously logged into LinkedIn on your computer, LinkedIn remembers this and will present you a different login screen, which might cause false positives or false negatives. Remember to at least clear out cookies between scans!
Good luck in your investigations!
Best Wishes,
AccentuSoft
